Client certificates
Use client certificates to authenticate your API checks to APIs that require mutual TLS (mTLS) authentication, or any other authentication scheme where the requester needs to provide a certificate.
Each client certificate is specific to a domain name, e.g. acme.com and will be used automatically by any API checks
targeting that domain.
Client certificates are available on the Enterprise plan only
Adding a certificate
Go to the Client Certificates tab on the Account settings screen.
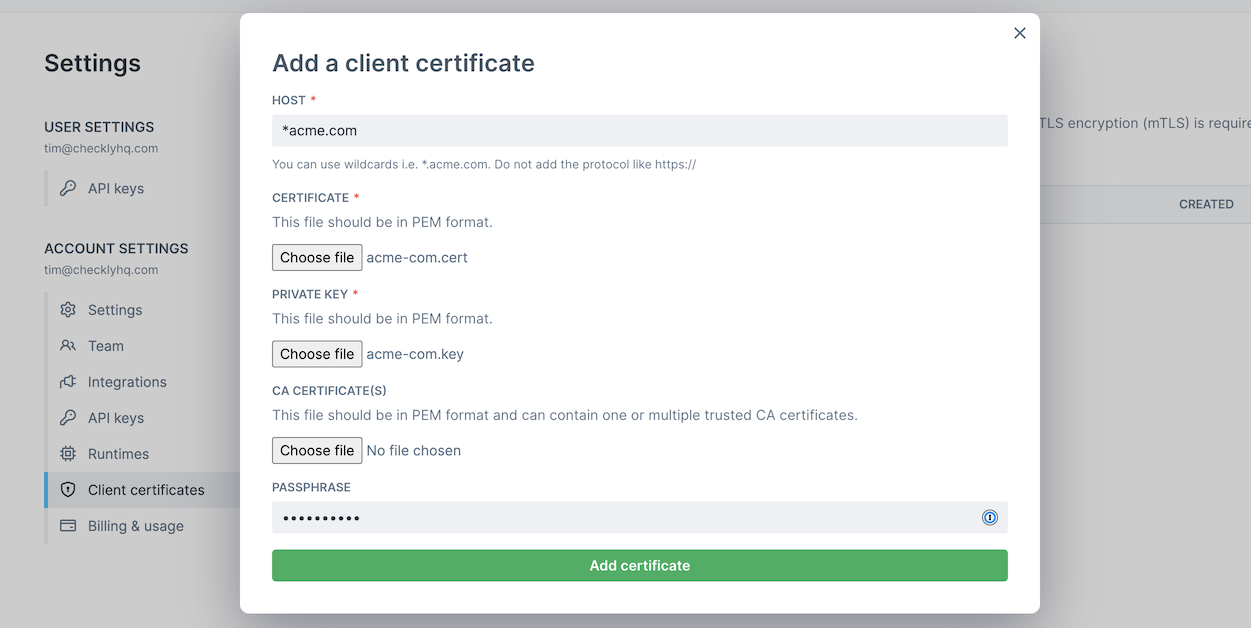
- Click “Add client certificate”.
- Provide the host name for the certificate. You can use wildcard like
*.acme.com. Under the hood we use minimatch - Select the certificate file and private key file. Both need to be in
PEMformat. - If your client certificate requires a custom Certificate Authority, you can add another
PEMfile that contains one or more concatenated CA certificates. - If you provided a passphrase when generating your certificate and private key files, provide it in the passphrase input. You can leave it empty if no passphrase is needed.
Note that your passphrase will be encrypted at rest, in transit and only used at very end when executing your API check.
Using a certificate
Client certificates are automatically used by API checks that match the host name of the certificate. Client certificates are active account wide and cannot be limited to a specific group.
You can add multiple certificate for the same host. In this case we match the certificate by the following rules:
- The most recently added certificate that matches the host name wins. This goes for both full hostname and ones with wildcards.
- A certificate with a full hostname wins over one that matches on a wildcard, e.g.
www.acme.comwins from*.acme.comfor the hostwww.acme.com
Editing a certificate
Client certificates cannot be edited. You can only remove or add client certificates.
Removing a certificate
You can remove a certificate by going to Client Certificates tab and clicking the delete icon. Note that any API checks that require a client certificate will start failing.
Known limitations
-
Because we need to match your certificate to your target endpoint for your API checks, you cannot change the
request.urlin a setup script as described here. -
We do not support
PKCS12certificate bundles. You can convert yourPKCS12bundles toPEMformat usingopenssl
openssl pkcs12 -in <CERT>.p12 -out <PRIVATE_KEY>.key -nodes -nocerts
openssl pkcs12 -in <CERT>.p12 -out <CERTIFICATE>.cert -nokeys
Last updated on April 25, 2024. You can contribute to this documentation by editing this page on Github